Double-click the hosts file. The messages displayed may be similar to the following: By default, this is C: What to do now Manual removal is not recommended for this threat. When conflicts arise on the profile or with the file, the application may be unable to transmit data between the necessary files.
| Uploader: | Zulujin |
| Date Added: | 6 August 2013 |
| File Size: | 10.67 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 77091 |
| Price: | Free* [*Free Regsitration Required] |
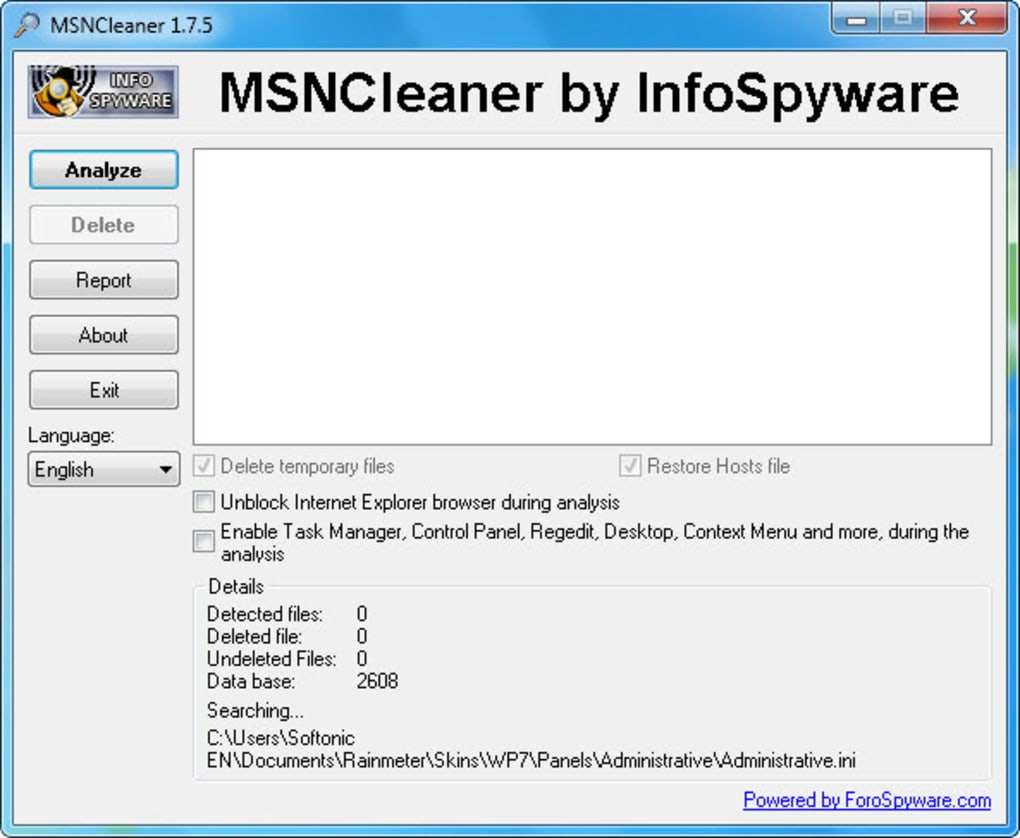
The location of the hosts file may vary and some computers may not have this file. Scan your computer Step 3: For instructions refer to the document: Some MSN viruses edit the registry and deny execution to msncleaner. Take these steps to help prevent infection on your computer.
April 26, Updated: She is on Messenger, and sends the repair utilities out to msncleanrr friends, because they know her Dad is a PC Tech. Windows Live Password reveal. Nov 20, Posts: Learn about other threats. For detailed instructions read the document: Are you the author? Avendog is a worm that attempts to spread by copying itself to removable drives and opens a back door on the compromised computer.
Worm:Win32/ threat description - Microsoft Security Intelligence
Therefore, antivirus programs or tools cannot remove threats in the System Restore folder. Close Notepad and save your changes when prompted. Download and execute arbitrary files.
When that happens, they can be very difficult to detect and remove, but using a comprehensive system scan usually detects them and allows you to safely remove them. You should download the definitions from the Symantec Security Response Web site and manually install them.
For example, one variant was observed to use the following:. I just may try it on a junk system to see what it does.
Using this backdoor, an attacker can perform the following actions on an affected machine: For more information, see.
For Norton AntiVirus consumer products: As a result, System Restore has the potential of restoring an infected file on your computer, even after you have cleaned the infected files from all the other locations.
As an example, some variants use the following messages:.
GX may also be able to perform one or more of the following additional activities:. For the moment, what you posted cured all the problems they had for Messenger.
These messages will not appear when the computer is restarted after the removal instructions have been fully completed. GX copies itself to "" and sets the attributes for this copy to read only, hidden and system.
Worm:Win32/Pushbot.gen
mencleaner Unless you have experience managing the processes and tasks on your machine, it is best to allow a system scanner or registry scanner to handle those tasks. Symptoms System Changes Symptoms may change among variants of the Worm: Presence of the following registry modification: How to configure Ese AntiVirus to scan all files.
Once you have restarted in Safe mode, run the scan again. However, files do become corrupt at times and some malicious files are disguised to represent known, secure system files. It then launches the new copy of itself, and deletes the original.

No comments:
Post a Comment